ISSN
2307–3489 (Print), ІSSN
2307–6666
(Online)
Наука
та прогрес транспорту. Вісник
Дніпропетровського
національного університету залізничного
транспорту, 2016,
№
5
(65)
АВТОМАТИЗОВАНІ
СИСТЕМИ УПРАВЛІННЯ НА ТРАНСПОРТІ
АВТОМАТИЗОВАНІ
СИСТЕМИ УПРАВЛІННЯ
НА
ТРАНСПОРТІ
UDC
656.25-047.58
M. Franekowa1*,
P. Lüley2*
1*Faculty
of Electrical Engineering, University of Žilina, Univerzitná St.,
8215/1, Žilina, Slovak Republic, 01026,
tel.
+ 421 (041) 513 33 46, e-mail maria.franekova@fel.uniza.sk
2*Faculty
of Electrical Engineering, University of Žilina,
Univerzitná St.,
8215/1, Žilina, Slovak Republic, 01026,
tel. +421 (041) 513 33 46, e-mail
peter.luley@fel.uniza.sk
ModelLing of safety-related
communications for
railway
applications
Purpose. The authors
according to requirements of the standard valid for safety-related
communication between interlocking systems (EN 50159) analyze the
situation of message undetected which is transmitted across BSC
channel. The main part is orientated to description of model with CRC
code used for messages assurance across noise communication channel.
Methodology. For mathematical description of encoding,
decoding, error detection and error correction is used algebra of
polynomials. Findings. The determination of the intensity of
dangerous failure caused by the electromagnetic interference was
calculated. Originality. To obtain information on the
probability of undetected error in transmission code and safety code
and on the intensity of dangerous failure from the motel it was
created program with graphical interface. To calculate the
probability of undetected error for any block code (n, k) was created
a supporting program that displays the probability of undetected
error for selected interval of error bit rate. Practical value.
From the measured and calculated values obtained by the
simulation one can see that with increasing error bit rate is
increasing also intensity of dangerous failures. Transmission code
did not detect all corrupted messages therefore it is necessary to
use safety code independent on transmission code in safety-related
applications. CRC is not able to detect errors if all bits are
logical 0.
Keywords: safety integrity level;
railway applications; safety-related communications; safety code;
CRC; Matlab; modeling
Introduction
If the
safety-related electronic system transfers information between
different entities then the communication system is also part of a
safety-related system and must be demonstrated that the transfer
between end terminals is safe and in compliance with standard EN
50159 [5].
Safety-related communication system performs and fulfils safety
functions with defined level of safety. Such a system includes a
safety-related communication layer which contains all necessary
mechanisms to ensure safety-related transfer of data [8].
Selection and use of a safety code and other recommended techniques
depends on whether is the possible unauthorized access to the system
or not. This fact is very significant because in case of possible
unauthorized access (malicious attacks) it is necessary to use
cryptographic techniques with secret key. If there is no possibility
of unauthorized access to the transmission system it is used
non-cryptographic safety code (type A0). If the unauthorized access
is possible we can achieve the safety by the transmission functions
related with safety with the use of cryptographic mechanisms (type
A1). Further is for this case used term cryptographic safety code.
In case of possible unauthorized access can be used separate access
protection layer (type B0 or B1).
Corruption of the message
during transmission can be caused by the network user, by the
failure of transmission medium, by the interference of messages or
by electromagnetic noise. Errors of this type are categorized as
unintentional attacks. They can be detected by the CRC (Cyclic
Redundancy Check) or by the CS (Check Sum). Evidence of safety with
respect to the safety integrity level and the nature of the
safety-related process must demonstrate appropriateness of:
probability of the detection of random error types and ability to
detect all types of expected message corruption systematic types.
Safety code must be independent
of the transmission code what can be achieved in two ways. One is to
use different encryption algorithms and the second is to use
different configuration parameters of the same algorithm. To meet
the required safety integrity level must be the probability of
undetected errors below specified limit. Safety code must be able to
detect transmission faults (e.g. impact of EMI) and systematic
faults in untrusted transmission system caused by hardware failures.
Safety code must also be able to detect typical faults of
transmission system.
In the paper we work with the
message type A0 because we do not expect unauthorized access to the
transmission system. Each message will be secured with
non-cryptographic safety code CRC-r.
Characteristic
of safety code
Cyclic code
is the most used code that can detect several multiple burst of
errors. This code is one of the linear codes
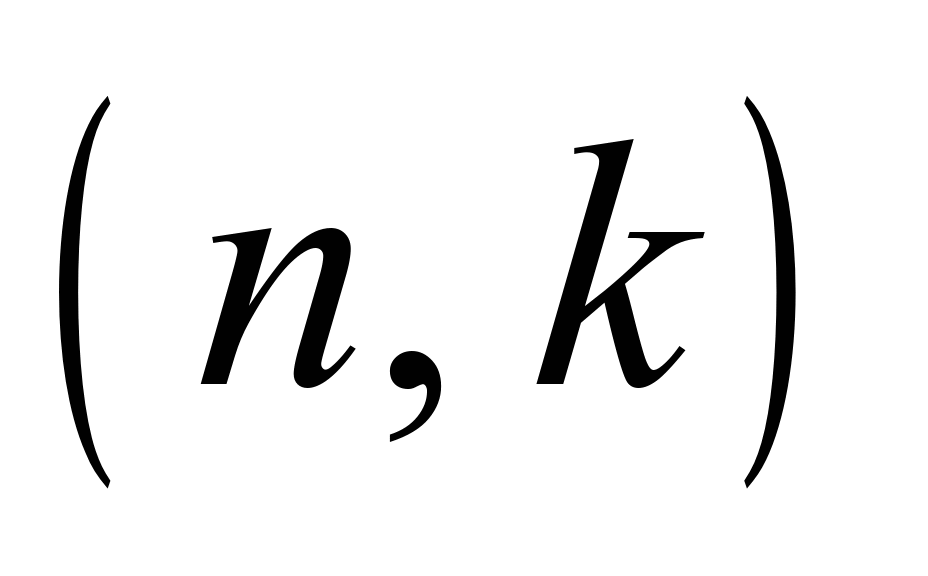 ,
for which is applicable the linearity property and also property
that cyclic shift of code word creates again code word belonging to
the code [6].
This feature is used in the construction of encoders, mainly by the
use of linear shift register with feedback. From the group of cyclic
codes in most communication protocols are used block systematic CRC
codes marked CRC-r (where
,
for which is applicable the linearity property and also property
that cyclic shift of code word creates again code word belonging to
the code [6].
This feature is used in the construction of encoders, mainly by the
use of linear shift register with feedback. From the group of cyclic
codes in most communication protocols are used block systematic CRC
codes marked CRC-r (where
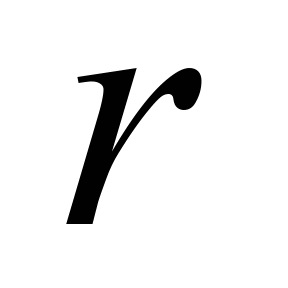 is the number of redundant bits in the
code word with length of
is the number of redundant bits in the
code word with length of
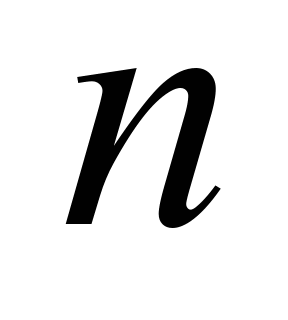 bits). For mathematical description of encoding, decoding, error
detection and error correction is used algebra of polynomials [7].
bits). For mathematical description of encoding, decoding, error
detection and error correction is used algebra of polynomials [7].
If is used
the safety code in transmission system it is necessary to
demonstrate probability of undetected error during transmission
below the limit defined by particular application or standard to
ensure the required safety level. Therefore it is necessary to
calculate the maximum value of probability of undetected error of
code word in the transmission system for every safety code. In case
of syndrome detecting techniques we look for event when syndrome is
zero (error was not detected) but during the transmission of the
code word occurred error. This case is mathematically expressed by
probability of code word error
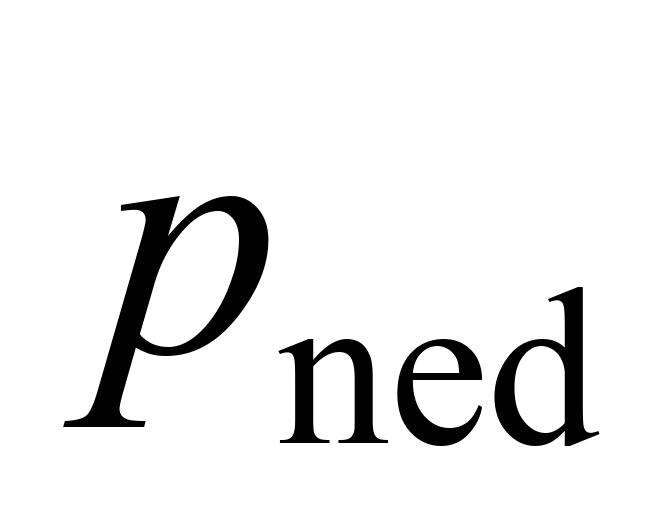 depending on the error bit rate
depending on the error bit rate
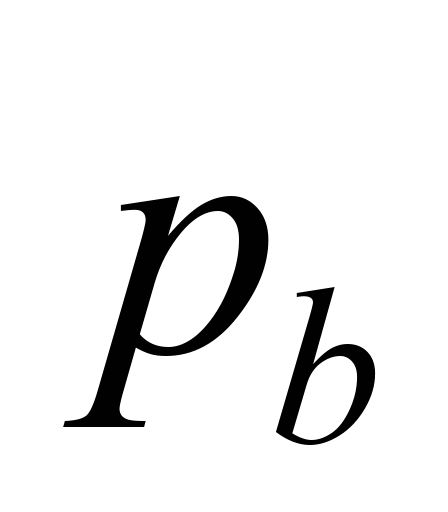 of used channel. In the calculation are used statistical values of
error bit rate of particular transmission speeds or if it is
possible for particular application the channel is tested.
of used channel. In the calculation are used statistical values of
error bit rate of particular transmission speeds or if it is
possible for particular application the channel is tested.
When
calculating the probability of undetected errors are considered only
errors arising due to interactions that cause the interchange of
symbols. Errors to the improper synchronization are resolved by
other safety means. The probability of undetected error for codes
with unknown weight function can be calculated by following equation
[4]:
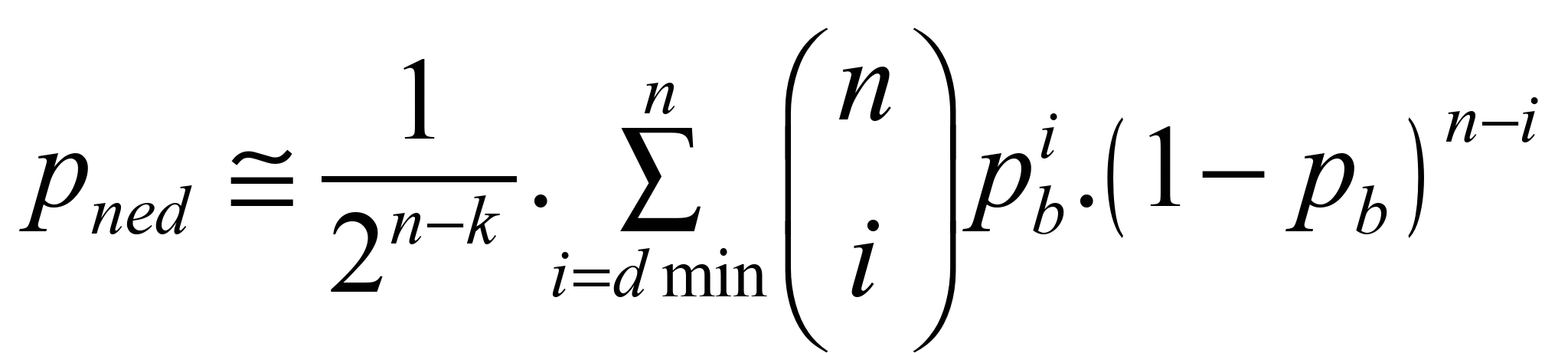 . (1)
. (1)
If the
conjunction of n
and
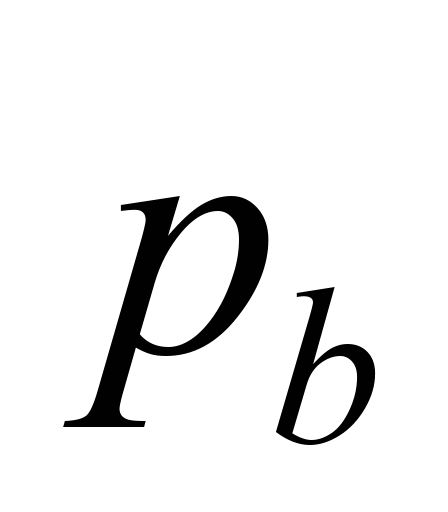 is much smaller than one (
is much smaller than one (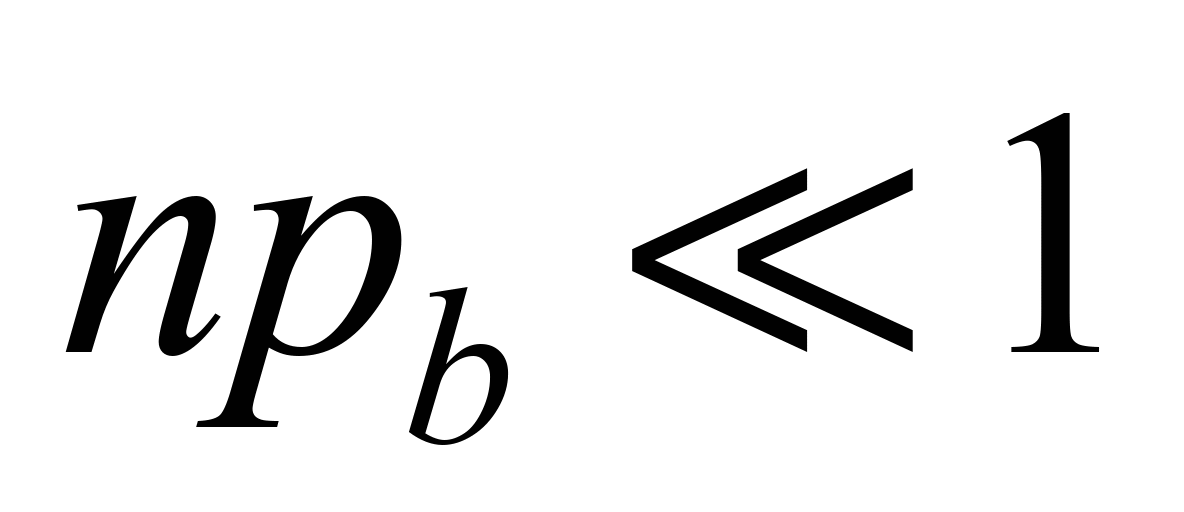 )
the sum can be approximated by the first number of the sum. The
equation 1 can be adjusted to following:
)
the sum can be approximated by the first number of the sum. The
equation 1 can be adjusted to following:
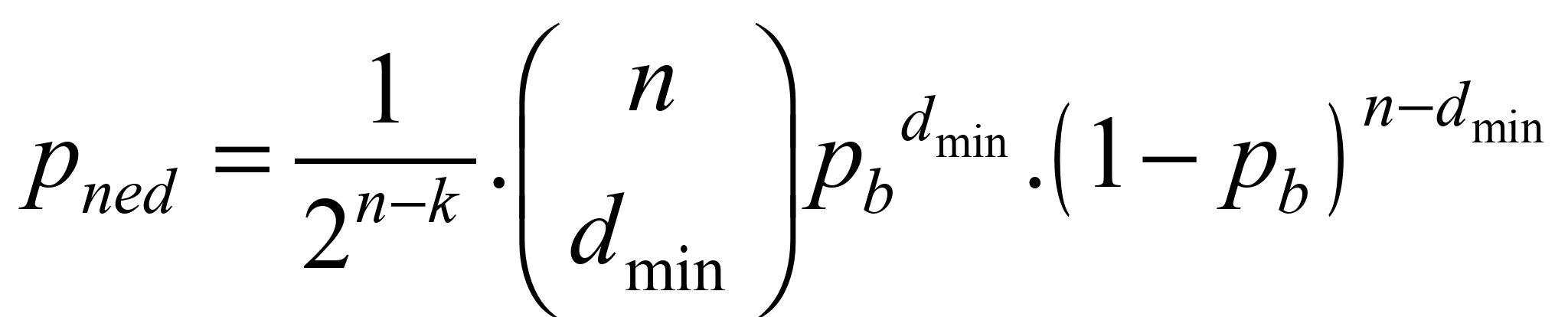 , (2)
, (2)
where:
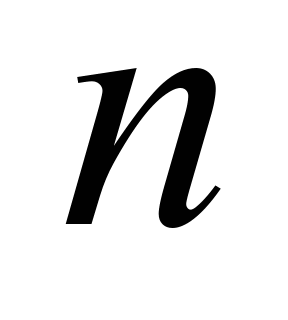 – total number of code bits,
– total number of code bits,
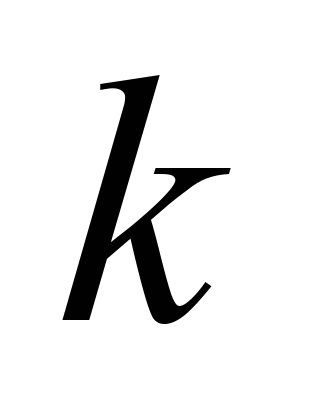 – number of information part bits,
– number of information part bits,
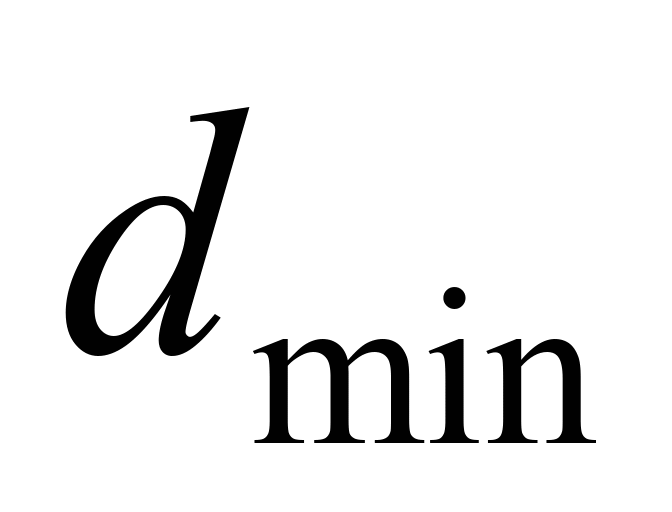 – minimum Hamming distance,
– minimum Hamming distance,
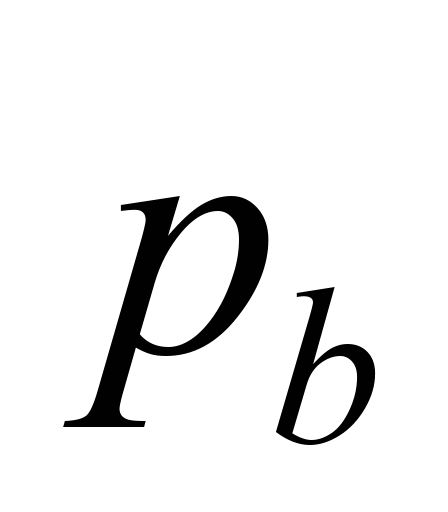 – error bit rate of the communication channel.
– error bit rate of the communication channel.
The minimum
Hamming distance
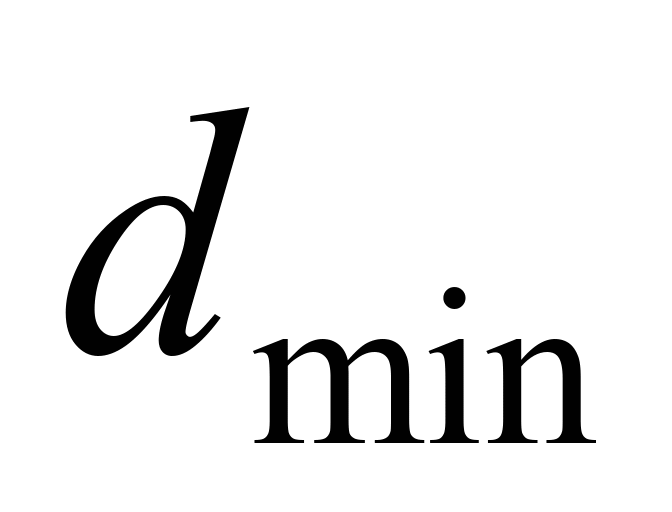 and the length of code word
and the length of code word
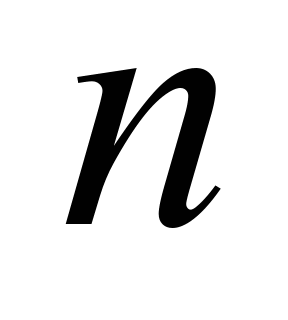 are the basis for the construction of block codes. The systematic
block code
are the basis for the construction of block codes. The systematic
block code
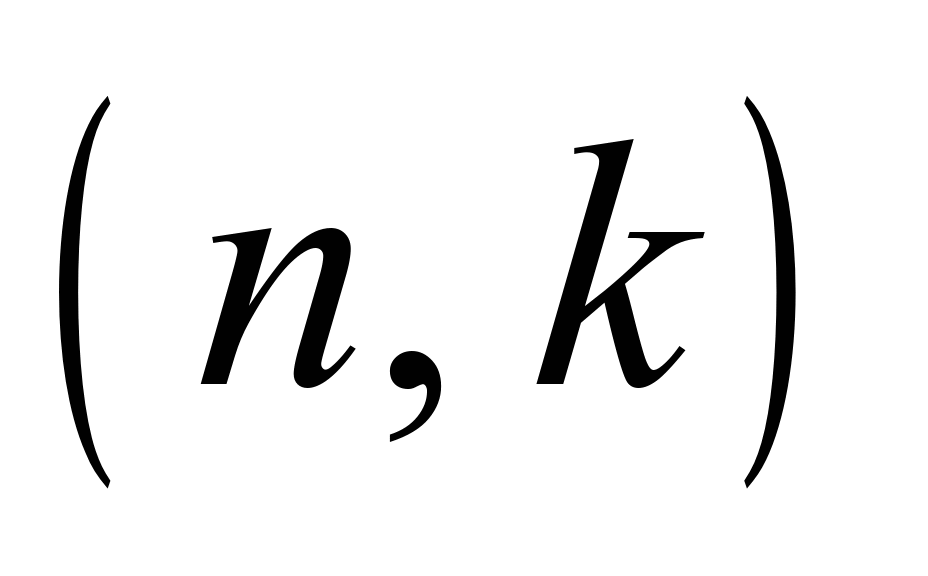 has the upper limit of achievable minimal Hamming distance given by
Varshamov-Gilbert inequality. For odd values of
has the upper limit of achievable minimal Hamming distance given by
Varshamov-Gilbert inequality. For odd values of
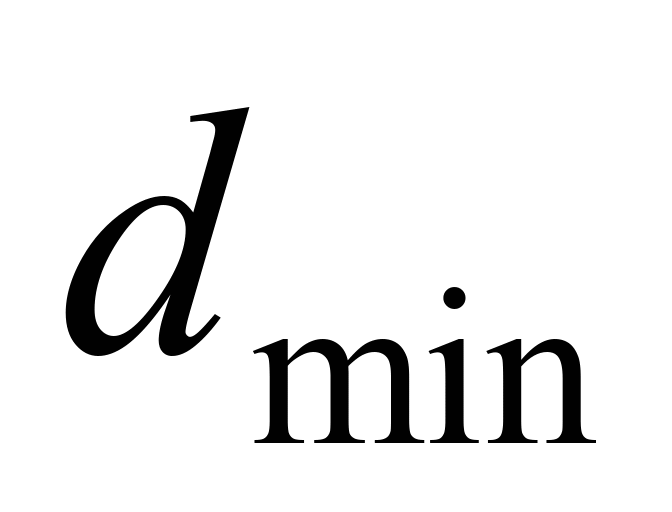 applies equation 3 and for even values of
applies equation 3 and for even values of
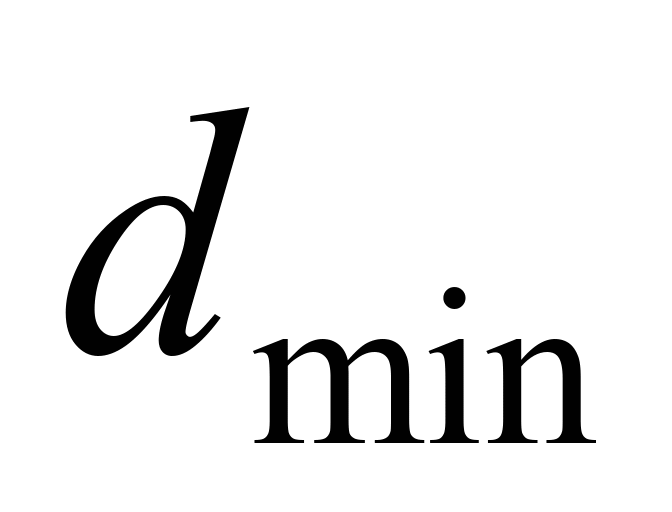 applies equation 4. Codes where
these two equations are equal are called perfect codes [3].
applies equation 4. Codes where
these two equations are equal are called perfect codes [3].
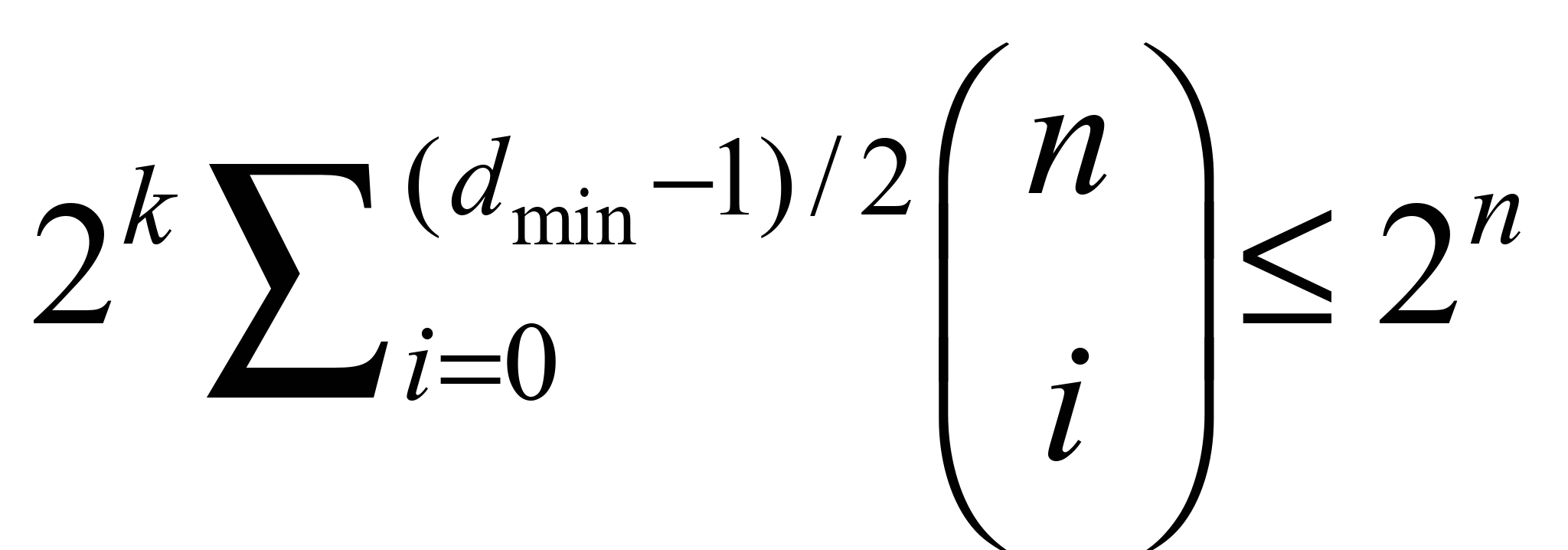 , (3)
, (3)
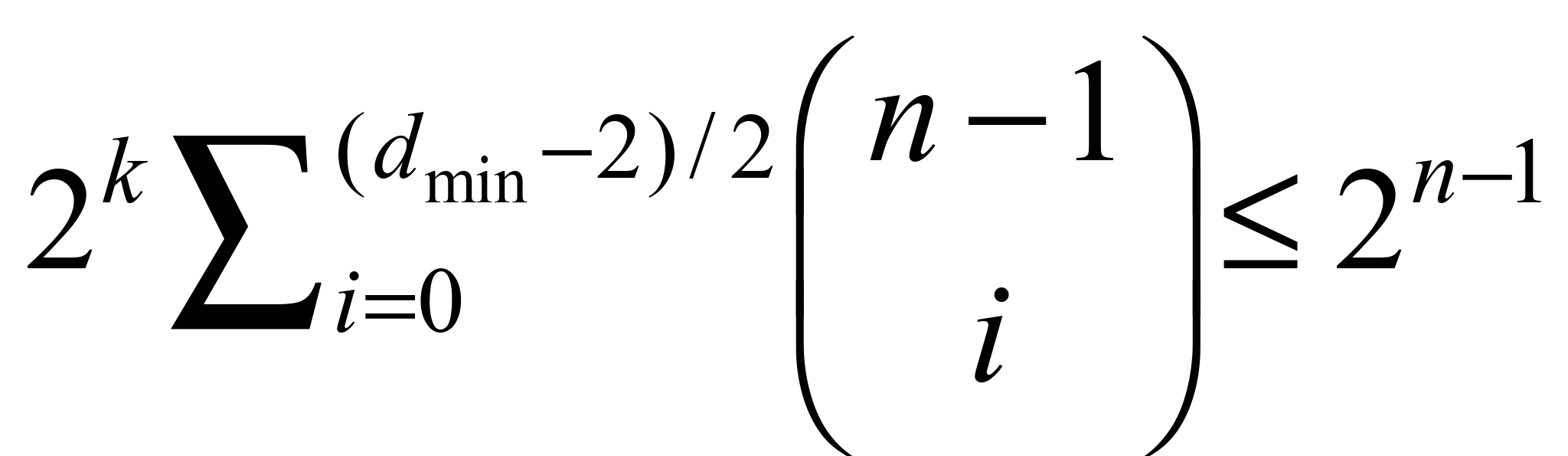 . (4)
. (4)
Error
probability calculated according to the equation 2 limits to the
value
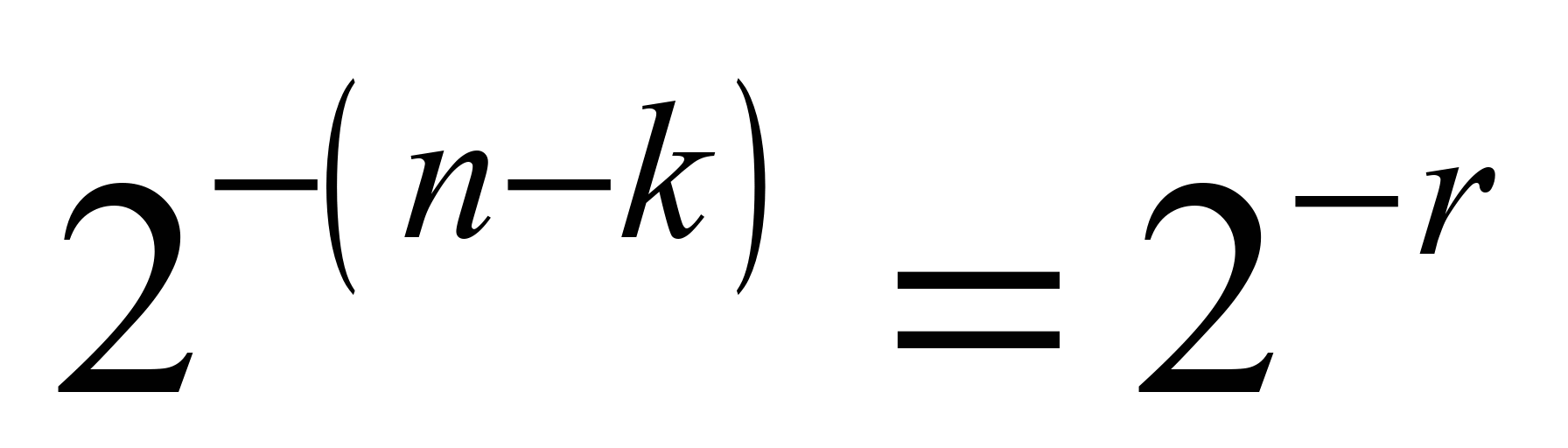 ,
what is the highest residual error rate of the code (equation 5).
This value is stated as maximum value of undetected error for CRC-r
codes [5].
The probability of undetected error can be then calculated by the
following equation:
,
what is the highest residual error rate of the code (equation 5).
This value is stated as maximum value of undetected error for CRC-r
codes [5].
The probability of undetected error can be then calculated by the
following equation:
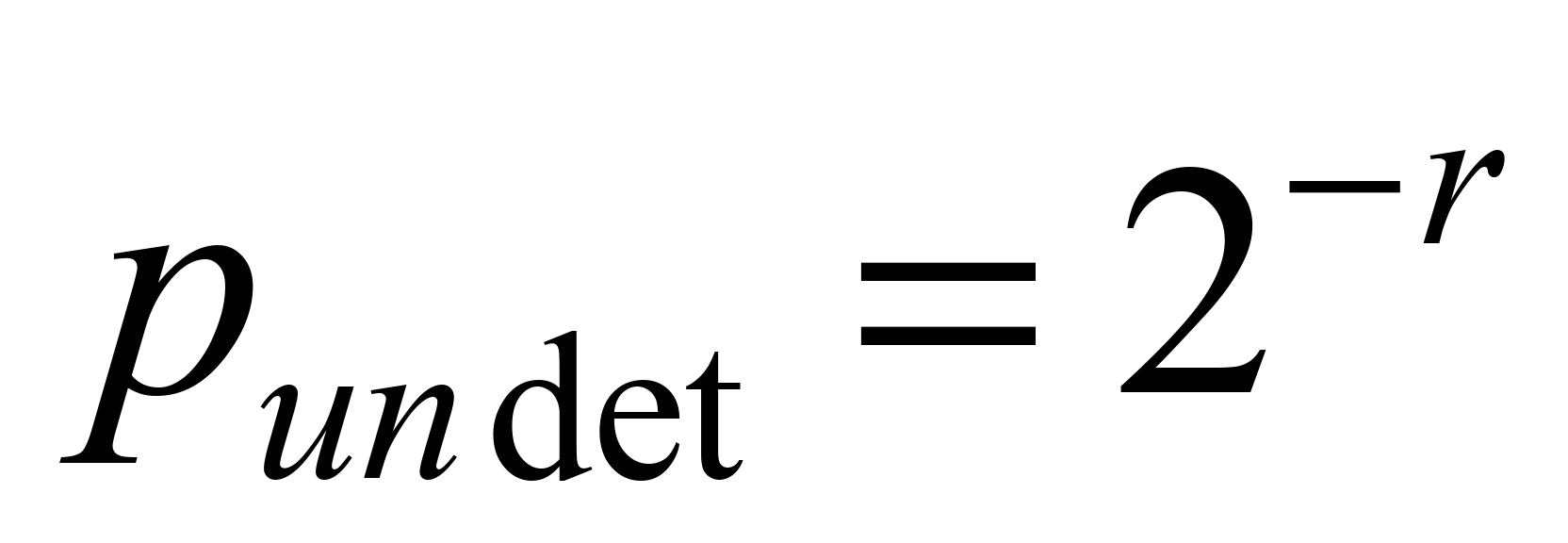 , (5)
, (5)
where:
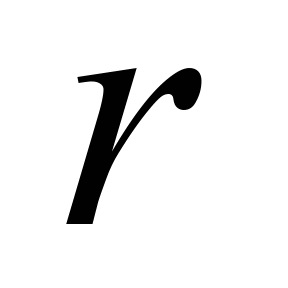 – number of redundant bits.
– number of redundant bits.
If the error
is not detected by transmission code nor safety code while the data
integrity was corrupted by EMI during the transmission of the
message the intensity of dangerous failure caused by EMI
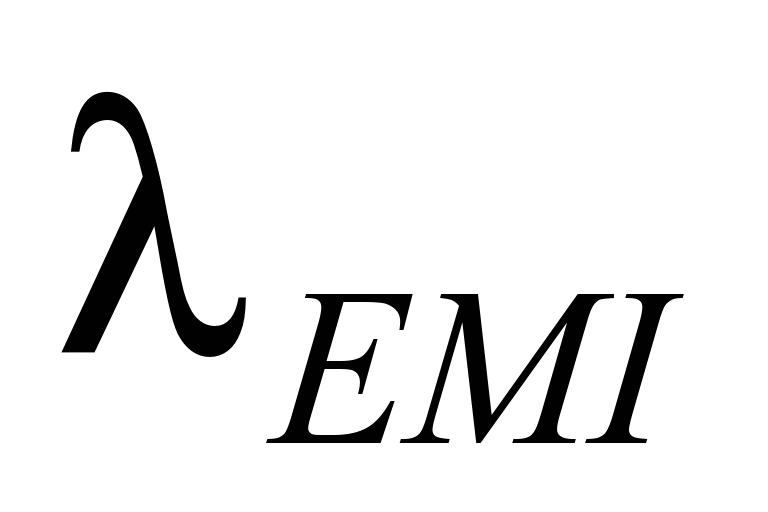 is calculated according to equation 6 [6]:
is calculated according to equation 6 [6]:
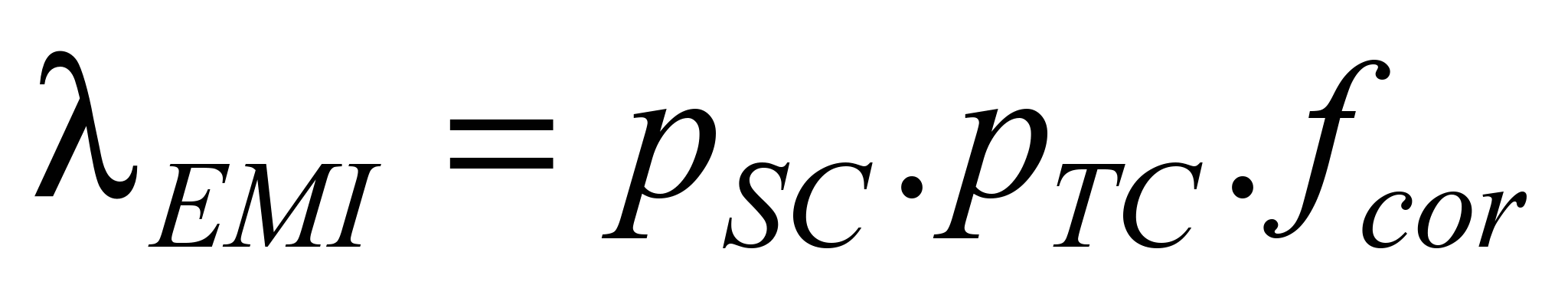 , (6)
, (6)
where:
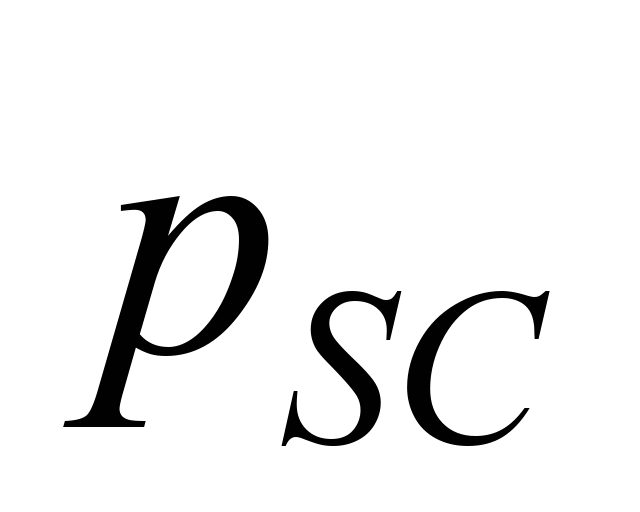 is the probability of undetected failure of safety code,
is the probability of undetected failure of safety code,
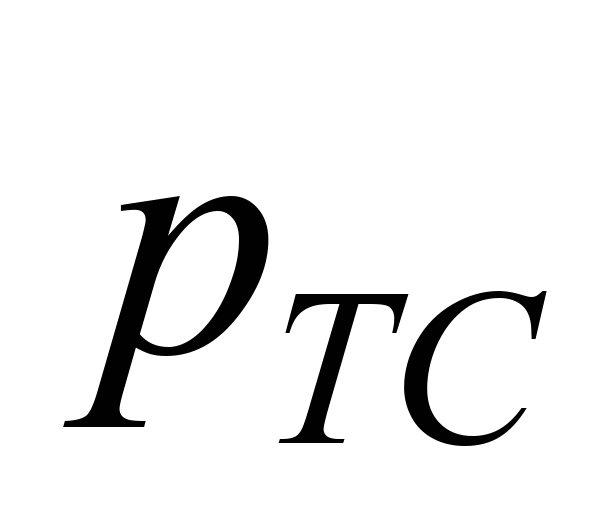 is the probability of undetected failure of transmission code,
is the probability of undetected failure of transmission code,
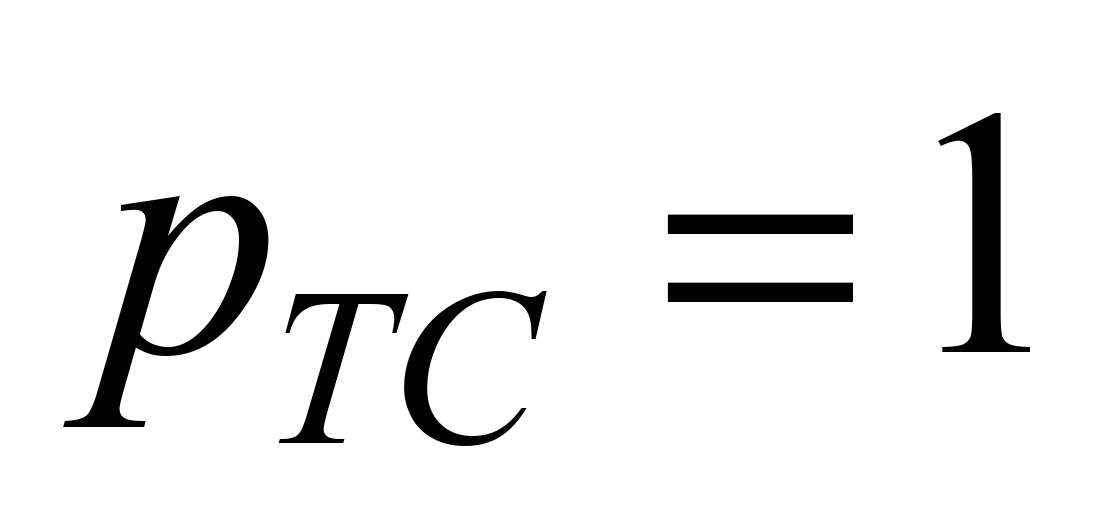 if the transmission system does not
include a channel encoder and channel decoder of transmission code,
if the transmission system does not
include a channel encoder and channel decoder of transmission code,
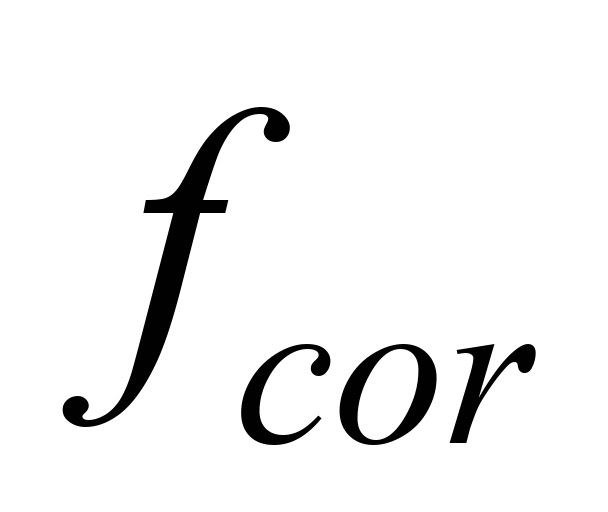 is the frequency of occurrence of corrupted messages. In case of
cyclic transmission of messages can be easily determined. In case of
non-cyclic transmission of messages is this value estimated or set
to the worst case scenario – all messages generated from the
source are corrupted.
is the frequency of occurrence of corrupted messages. In case of
cyclic transmission of messages can be easily determined. In case of
non-cyclic transmission of messages is this value estimated or set
to the worst case scenario – all messages generated from the
source are corrupted.
Description
of realized model
Realized
model of safety-related communication system with transmission code
and safety code is shown in Fig. 1. In the figure is the scheme
composed of seven blocks. Communication system consists of
transmission system and two terminal equipment’s TE1
and TE2.
Transmission system is composed of a communication channel CCH,
encoder of transmission code ETC,
decoder of transmission code DTC,
encoder of safety code ESC
and decoder
of safety code DSC.
The transmission system is untrusted if it contains only a
communication channel and transmission code. The safety integrity
level can be in this case defined as SIL 0. To achieve higher level
of safety integrity SIL 1 to SIL 4 we have to add safety code for
elimination of communication errors which are not detected via
transmission code. The SIL level depends on the selected
safety code.
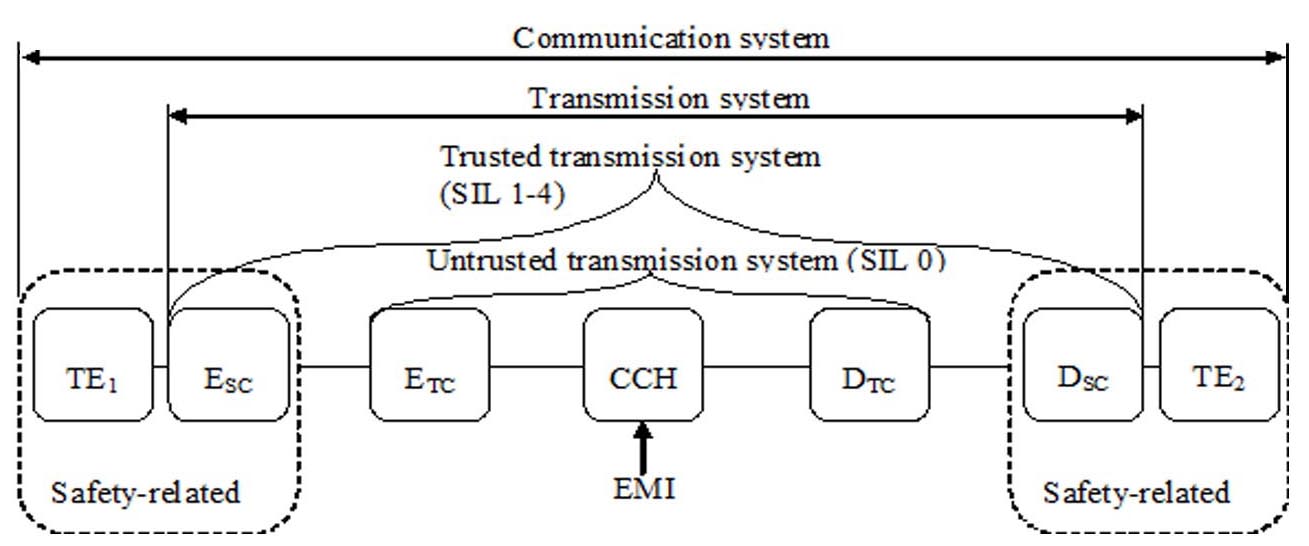
Fig.
1. Safety-related communication system for two-point connection
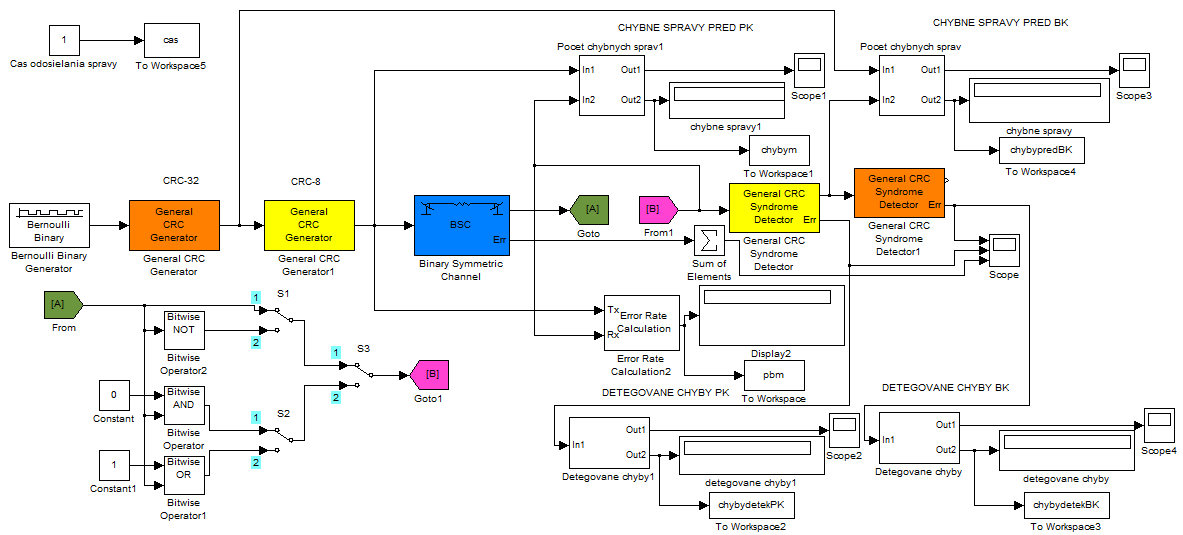
Fig.
2. Model with a safety code and transmission code realized in Matlab
[2]
In Fig. 2 is
shown the model simulating the transfer of n messages secured with
safety code and transmission code which was constructed in software
tool Matlab, version 7.10.0 (R2010a) and Communications System
Toolbox library [2].
The model is constructed to
simulate the transmission of messages through safety-related
communication system secured by transmission code and safety code
for two-point connection. From the point of view of ensuring the
transmission we are using the safety code and transmission code
based on CRC-r. Length of information part of the message was set to
64 bits. In order to ensure the independence of both types of codes
was the generating polynomial of transmission code selected from
standardized polynomials. For safety analysis we used generating
polynomial of 8th degree type G(x)= x8+x2+x+1, which is used for
example in ATM link protocol. Safety code generating polynomial was
also selected from standardized polynomials for safety-related
applications. There was selected polynomial of 32nd grade
G(x)=x32+x30+x27+x25+x22+x20+x13+x12+x11+x10+x8+x7+x6+x5+x4+1,
which
is used for example by the European Train Control System ETCS and if
used separately it provides integrity level SIL 2. Model is designed
so that we can simulate different error pattern. To trigger them we
use three switches (S1, S2, S3). If we want to simulate transmission
where the messages are affected only by functional block of binary
symmetric channel (which generates random errors) S1 must be in
position 1, on the position of S2 does not matter and S3 must be in
position 1. If we want to simulate transmission where the messages
are affected by functional block of binary symmetric channel and
subsequently negated the position of switches is as follows: S1 –
position 2, S2 – does not matter, S3 – position 1. If we want to
simulate transmission where all bits are set to logical 0 the
position of switches is as follows: S1 – does not matter, S2 –
position 1, S3 – position 2. If we want to simulate transmission
where all bits are set to logical 1 the position of switches is as
follows: S1 – does not matter, S2 – position 2, S3 – position
2.
Results and comments
During the
time simulations of safety-related messages we were changing the bit
error rate (BER) of the binary symmetric channel (BSC) by changing
of BER in the range 1.10-8 to 0,5 (values less than 10-8 have shown
very low error rate). Time of the simulation was set to 100000 s for
every error bit rate of binary symmetric channel to simulate
transfer of 100000 messages with length 104 bits (64 bits of
information part, safety code 32 bits and transmission code 8 bits).
Each second was sent one message [2].
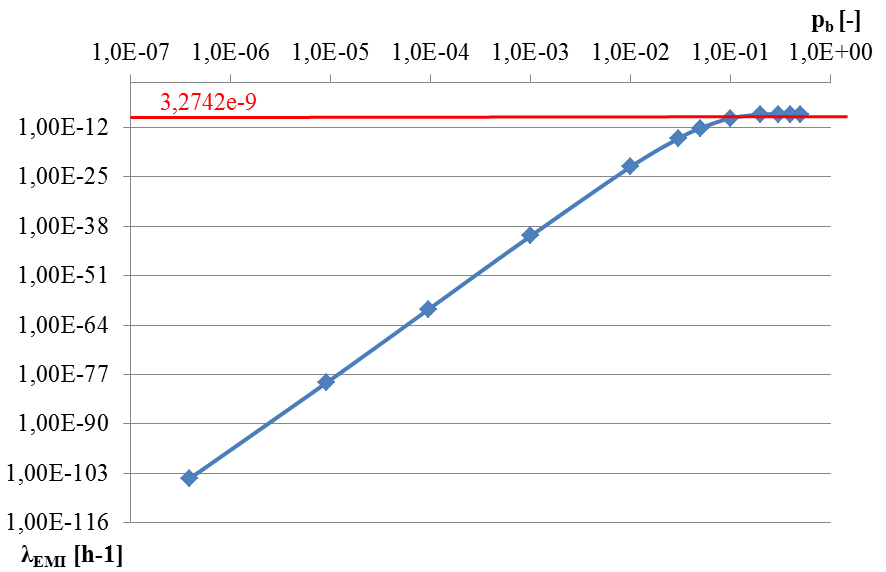
Fig.
4. Dependence of
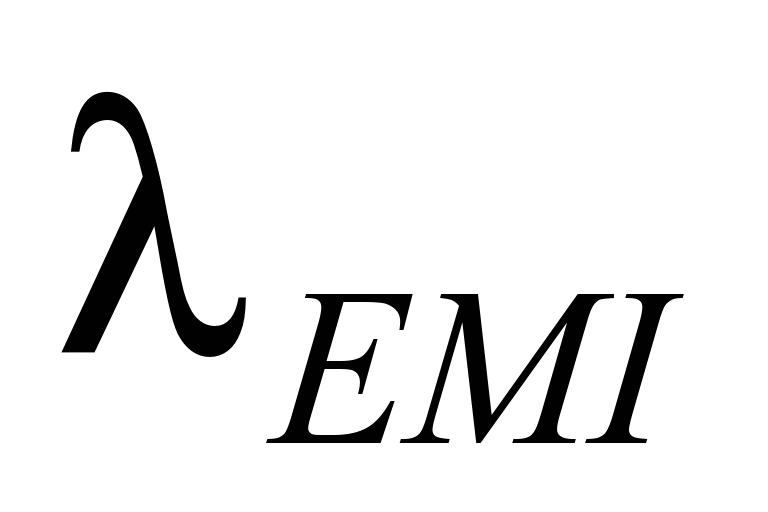 on
on
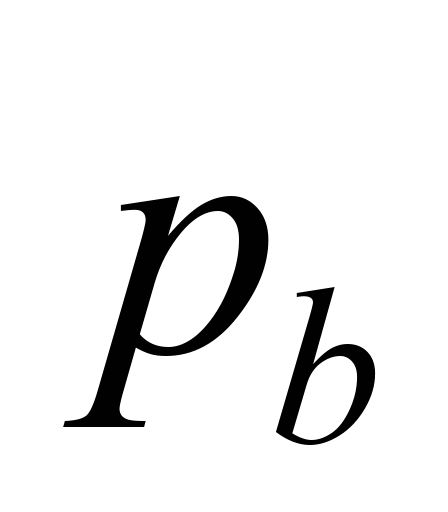 [4]
[4]
In the Fig.
2 is shown intensity of dangerous failures caused by EMI in closed
transmission system which is assured by transmission and safety
codes depending on the real BER of the communication channel. The
value (3,2742e-9) is the worst intensity of dangerous failure. This
is calculated as conjunction of the value of worst probability of
transmission code (2-8),
value of worst probability of safety code and (2-32)
and the frequency of corrupted massages, when all messages are
considered as corrupted (3600). This implies that such transmission
system complies with requirements for the safety intensity level SIL
4 classified for all system with high demand (10-9
≤ THR ≤ 10-8).
Conclusions
The number of applications with
higher SIL (Safety Integrity Level) for which is necessary to
provide evidence of safety not only for hardware parts and software
parts but also for the communication system is growing. The authors
are in this papers dealing with the issue of safety-related
communication and types of failures that may occur during
transmission of safety-related messages. We focused on the
requirements for the safety code according to standard EN 50159 with
special attention to the cyclic code on the CRC principle. According
to requirements of the standard it is necessary to demonstrate that
transmission via real communication channel with safety code meets
the required safety integrity level.
The main
part of the article was orientated to model realization that
simulates transmission of safety-related messages via communication
system with closed transmission system at the level of two-point
connection. We simulated transfer of messages for various settings
of bit error rate of communication channel (model BSC). We also
simulated transfer of messages in extreme fault condition as
inversion of the message, all bits in logical 0 and all bits in
logical 1. We applied limited binary error channel to test the
integrity of the transfer with CRC-r safety code and transmission
code for various lengths of simulated burst of errors. To obtain
information on the probability of undetected error in transmission
code and safety code and on the intensity of dangerous failure from
the motel we created program with graphical interface. To calculate
the probability of undetected error for any block code (n,
k) was
created a supporting program that displays the probability of
undetected error for selected interval of error bit rate. We can see
from the measured and calculated values obtained by the simulation
that with increasing error bit rate is increasing also intensity of
dangerous failures. Transmission code did not detect all corrupted
messages therefore it is necessary to use safety code independent on
transmission code in safety-related applications. CRC is not able to
detect errors if all bits are logical 0.
Acknowledgements
This work has been supported by
the Educational Grant Agency of the Slovak Republic (KEGA) Number:
008ŽU-4/2015: Innovation of HW and SW tools and methods of
laboratory education focused on safety aspects of ICT within safety
critical applications of processes control.
LIST OF REFERENCE LINKS
Białoń,
A. Bezpieczeństwo i ryzyko na przykładzie urządzeń sterowania
ruchem kolejowym / A. Białoń, M. Pawlik // Problemy kolejnictwa.
– 2014. – Z. 163. – P. 25–41.
Cauner,
R. Models of transmission systems with cyclic code generation via
SW tool Matlab for safety-related applications ;
Slovak Diploma work / R. Cauner
; University of Žilina.
– Žilina,
2015.
Clark,
G. C. Error–Correction Codes for Digital Communications / G. C.
Clark, Jr. and J. Bibb Cain. – New York : Plenum Press, 1988. –
422 p. doi: 10.1007/978-1-4899-2174-1.
Communication
security of industrial networks: in Slovak Komunikačná bezpečnosť
priemyselných sietí / M. Franeková, F. Kállay, P. Peniak, P.
Vestenický. – Žilina : EDIS ŽU, 2007.
EN
50159. Railway applications. Communication, signalling and
processing systems. Safety-related communication in transmission
systems. – 2010.
Franeková,
M. Modelovanie prenosu dát v prostredí Matlab, Simulink a
Communications Sytem Toolbox / M. Franeková, R. Pirník, L.
Pekár. – Žilina : Žilinská univerzita, 2014. – 218 p.
Muzikářová,
Ľ. Teória informácie a signálov / L.Muzikářová,
M. Franeková.
– Žilina : Žilinská univerzita, 2009. – 217 p.
Popov,
G. Methods of increasing reliability of Semi-Ergatic Systems in
extreme situation / G. Popov, M. Hristova, H. Hristov // Latest
Trend in Applied Informatics and Computing : Proc. the 3rd Intern.
Conf. on Applied Informatics and Computing Theory
(17.10–19.10.2012). – Barcelona, Spain, 2012. – P. 225–231.
М. ФРАНЕКОВА1*, П. ЛЮЛЕЙ2
1*Каф.
«Електротехніка»,
Жилінський університет,
вул. Університетська, 8215/1, Жиліна,
Словацька Республіка,
01026, тел.
+421 (041) 513 33 46, ел. пошта
maria.franekova@fel.uniza.sk
2*Каф.
«Електротехніка»,
Жилінський університет,
вул. Університетська, 8215/1, Жиліна,
Словацька Республіка,
01026, тел.
+421 (041) 513 33 46, ел. пошта
peter.luley@fel.uniza.sk
МОДЕЛЮВАННЯ ПРИСТРОЇВ ЗВ'ЯЗКУ,
ЩО ЗАБЕЗПЕЧУЮТЬ БЕЗПЕКУ на залізницях
Мета.
Відповідно до вимог стандартів до
безпечного зв’язку в системах
централізації (EN 50159) авторами
проаналізовано ситуацію невиявлених
повідомлень про помилку, яка передається
через канал двійкової синхронної
передачі. Основна частина статті описує
модель із кодом циклічної перевірки,
яка використовується для забезпечення
достовірності повідомлень, переданих
через канал зв’язку шумових перешкод.
Методика.
Для математичного опису кодування,
декодування, виявлення і корекції
помилок використовується алгебра
многочленів. Результати.
Для отримання інформації про ймовірність
невиявлення помилки в коді передачі
та коді безпеки, а також інформації про
інтенсивність небезпечних відмов, була
створена програма з графічним інтерфейсом.
Для того, щоб обчислити вірогідність
невиявлення помилки для будь-якого
блочного коду (n, k) була створена допоміжна
програма, яка відображає ймовірність
невиявлення помилки для обраного
інтервалу швидкості передачі бітів
помилки. Наукова новизна.
У статті розраховується визначення
інтенсивності небезпечних відмов,
викликаних електромагнітними перешкодами.
Практична значимість.
На основі виміряних та розрахункових
значень, отриманих за допомогою
моделювання, можна зробити висновок,
що зі збільшенням частоти появи бітів
помилки зростає також інтенсивність
небезпечних відмов. Код передачі не
може виявити всі пошкоджені повідомлення,
тому необхідно використовувати код
безпеки незалежно від коду передачі в
додатках, пов’язаних із безпекою. Код
циклічної перевірки не може виявити
помилки, якщо всі біти логічні 0.
Ключові слова: рівень повноти
безпеки; залізничні додатки; пристрої
зв’язків безпеки; код безпеки; CRC;
Matlab; моделювання
М. Франекова1*, П. ЛЮлей2
1*Каф.
«Электротехника», Жилинский
университет, ул. Университетская,
8215/1, Жилина, Словацкая Республика,
01026, тел. + 421 (041) 513 33 46, эл. почта
maria.franekova@fel.uniza.sk
2*Каф.
«Электротехника», Жилинский
университет, ул. Университетская,
8215/1, Жилина, Словацкая Республика,
01026, тел. +421 (041) 513 33 46, эл. почта
peter.luley@fel.uniza.sk
МОДЕЛИРОВАНИЕ
УСТРОЙСТВ связИ,
ОБЕСПЕЧИВАЮЩИХ
безопасностЬ
НА ЖЕЛЕЗНЫХ ДОРОГАХ
Цель.
В соответствии с требованиями стандартов
для безопасной
связи в системах
централизации (EN 50159)
авторами проанализирована ситуация
необнаруженных сообщений об ошибке,
которая передается через канал двоичной
синхронной передачи. Основная часть
статьи описывает модель с кодом
циклической проверки, используемую
для обеспечения достоверности сообщений,
передаваемых через канал связи шумовых
помех. Методика.
Для математического описания кодирования,
декодирования, обнаружения и коррекции
ошибок используется алгебра многочленов.
Результаты. Для получения
информации о вероятности необнаружения
ошибки в коде передачи и коде безопасности,
а также информации об интенсивности
опасных отказов, была создана программа
с графическим интерфейсом. Для того,
чтобы вычислить вероятность необнаружения
ошибки для любого блочного кода (n,
k) была создана вспомогательная
программа, которая отображает вероятность
необнаружения ошибки для выбранного
интервала скорости передачи битов
ошибки. Научная новизна.
В статье рассчитывается определение
интенсивности опасных отказов, вызванных
электромагнитными помехами. Практическая
значимость. На основе
измеренных и расчетных значений,
полученных с помощью моделирования,
можно сделать вывод, что с увеличением
частоты появления битов ошибки растет
также интенсивность опасных отказов.
Код передачи не обнаруживает все
поврежденные сообщения, поэтому
необходимо использовать код безопасности
независимо от кода передачи в приложениях,
связанных с безопасностью. Код циклической
проверки не может обнаружить ошибки,
если все биты логичны 0.
Ключевые слова:
уровень полноты безопасности;
железнодорожные приложения; устройства
связи безопасности; код безопасности;
CRC; Matlab;
моделирование
REFERENCES
Białoń A., Pawlik M. Bezpieczeństwo i ryzyko na
przykładzie urządzeń sterowania ruchem kolejowym. Problemy
kolejnictwa, 2014, z. 163, pp. 25-41.
Cauner
R. Models of transmission systems with cyclic code generation via
SW tool Matlab for safety-related applications. In: Slovak.
Diploma work, University of Žilina,
2015.
Clark
G.C., Jr. and J. Bibb Cain. Error–Correction Codes for Digital
Communications. New York, Plenum Press, 1988. 422 p. doi:
10.1007/978-1-4899-2174-1.
Franeková
M., Kállay F., Peniak P., Vestenický P. Communication security of
industrial networks: in Slovak, Komunikačná bezpečnosť
priemyselných sietí. Žilina, EDIS ŽU Publ., 2007.
EN
50159: Railway applications. Communication, signalling and
processing systems. Safety-related communication in
transmission systems. 2010.
Franeková
M., Pirník R., Pekár L. Modelovanie prenosu dát v prostredí
Matlab, Simulink a Communications Sytem Toolbox. Žilina,
Žilinská univerzita Publ., 2014. 218 p.
Muzikářová
Ľ., Franeková
M. Teória informácie a signálov. Žilina, Žilinská
univerzita Publ., 2009. 217 p.
Popov
G., Hristova M., Hristov H. Methods of increasing reliability of
Semi-Ergatic Systems in extreme situation. Latest Trend in Applied
Informatics and Computing: Proc. pf the 3rd Intern. Conf. on
Applied Informatics and Computing Theory (17.10-19.10.2012) (AICT
2012). Barcelona, Spain. WSEAS Press, 2012, pp. 225-231.
Prof. V. H. Sychenko, D. Sc.
(Tech.) (Ukraine) recommended this article to be published
Accessed: 19 May, 2016
Received: 15 Sept., 2016
doi © M.
Franekowa, P. Lüley,
2016
,
for which is applicable the linearity property and also property
that cyclic shift of code word creates again code word belonging to
the code [6].
This feature is used in the construction of encoders, mainly by the
use of linear shift register with feedback. From the group of cyclic
codes in most communication protocols are used block systematic CRC
codes marked CRC-r (where
is the number of redundant bits in the
code word with length of
bits). For mathematical description of encoding, decoding, error
detection and error correction is used algebra of polynomials [7].
depending on the error bit rate
of used channel. In the calculation are used statistical values of
error bit rate of particular transmission speeds or if it is
possible for particular application the channel is tested.
. (1)
is much smaller than one (
)
the sum can be approximated by the first number of the sum. The
equation 1 can be adjusted to following:
, (2)
– total number of code bits,
– number of information part bits,
– minimum Hamming distance,
– error bit rate of the communication channel.
and the length of code word
are the basis for the construction of block codes. The systematic
block code
has the upper limit of achievable minimal Hamming distance given by
Varshamov-Gilbert inequality. For odd values of
applies equation 3 and for even values of
applies equation 4. Codes where
these two equations are equal are called perfect codes [3].
, (3)
. (4)
,
what is the highest residual error rate of the code (equation 5).
This value is stated as maximum value of undetected error for CRC-r
codes [5].
The probability of undetected error can be then calculated by the
following equation:
, (5)
– number of redundant bits.
is calculated according to equation 6 [6]:
, (6)
is the probability of undetected failure of safety code,
is the probability of undetected failure of transmission code,
if the transmission system does not
include a channel encoder and channel decoder of transmission code,
is the frequency of occurrence of corrupted messages. In case of
cyclic transmission of messages can be easily determined. In case of
non-cyclic transmission of messages is this value estimated or set
to the worst case scenario – all messages generated from the
source are corrupted.